RemoteIoT VPC Networks: Examples, Setup & Best Practices
Are you struggling to manage your Internet of Things (IoT) devices securely and efficiently in today's rapidly evolving digital landscape? Mastering remote IoT VPC network examples is not just beneficial; it's absolutely essential for securing and optimizing your cloud infrastructure.
The convergence of cloud computing and the Internet of Things has sparked a revolution, fundamentally changing how businesses and individuals manage their IT infrastructure. This transformation has elevated the significance of secure, scalable, and efficient networking solutions, placing "remote IoT VPC network example" at the forefront of technological discussions. As businesses increasingly adopt remote operations, the ability to design and deploy Virtual Private Cloud (VPC) networks effectively becomes critical for maintaining robust, scalable IT infrastructures. The goal is to provide you with an in-depth understanding of designing and deploying remote IoT VPC networks. We'll go beyond the surface, offering practical examples and actionable insights.
Here's a look at the critical concepts involved in setting up a remote IoT VPC network:
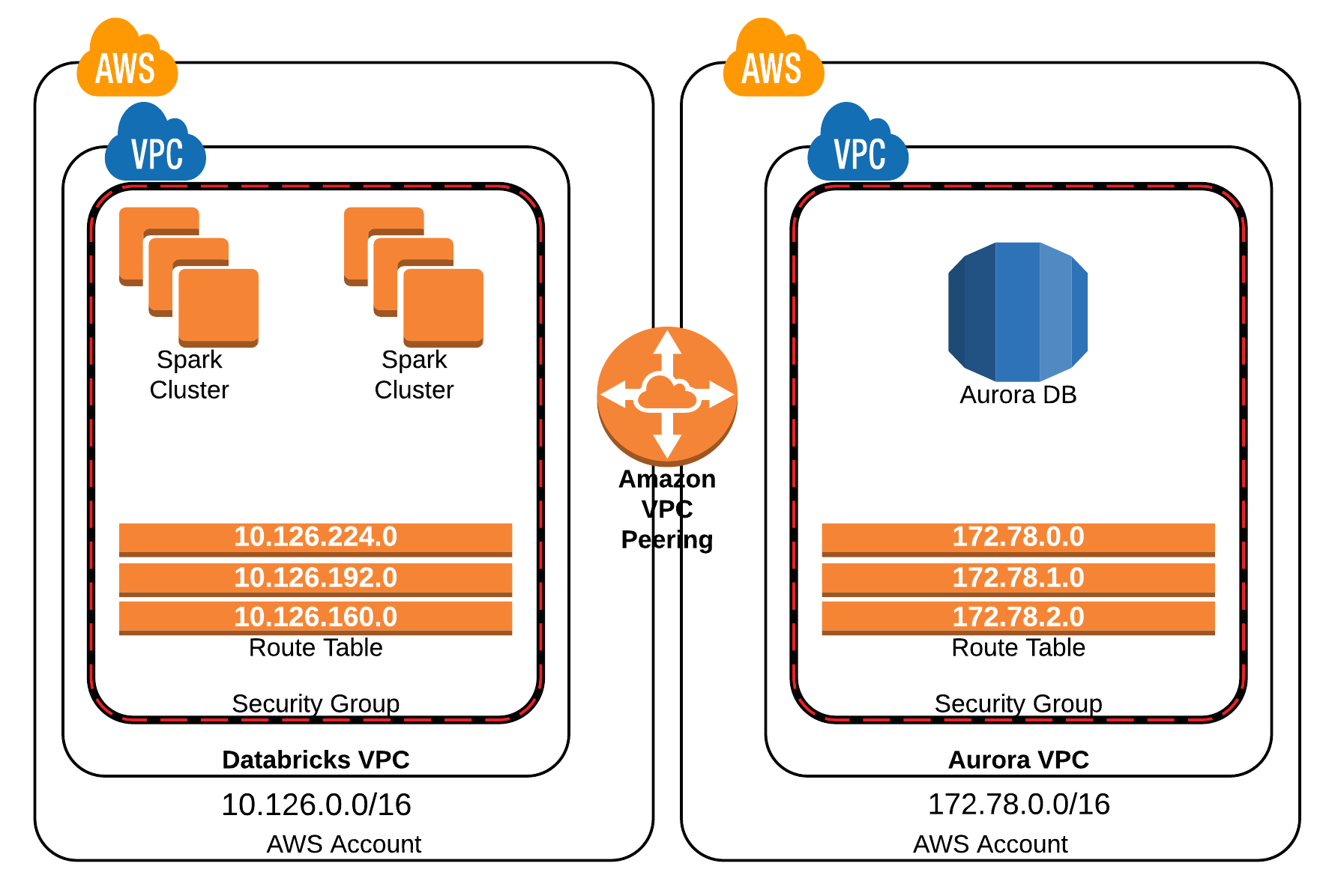
A Virtual Private Cloud (VPC) network is essentially your own isolated section within a cloud provider's infrastructure. Think of it as a private playground where you can control who gets in and what they can do. For remote IoT VPC network examples, this means creating an environment tailored specifically for IoT devices and applications. This article is dedicated to breaking down the fundamentals of Remote IoT VPC Networks, enabling you to implement secure and scalable IoT solutions.
The core of this approach lies in understanding and utilizing Amazon Web Services (AWS), a powerful platform for hosting and managing remote IoT setups. AWS offers a wide array of services, with the Virtual Private Cloud (VPC) being a key component. It allows you to create a private network tailored for your IoT devices, ensuring a secure and controlled environment.
However, establishing a remote IoT VPC network is not merely a matter of connecting devices; it demands a comprehensive grasp of cloud infrastructure, rigorous security protocols, and strategic network design. Whether you're a beginner or an advanced user, this exploration will provide you with the necessary insights to navigate the complexities of remote IoT VPC networks.
For the purpose of this article, the primary focus will be on Remote IoT VPC Network Example. This concept has become a critical topic for businesses and developers seeking to securely connect their Internet of Things (IoT) devices to cloud environments. The article will delve into the various aspects of designing and deploying Remote IoT VPC Networks, offering practical examples and actionable insights.
A deeper understanding of remote IoT VPC network examples is crucial for businesses and individuals who aim to optimize their IoT infrastructure. The benefits of leveraging VPC technology for remote IoT include enhanced data privacy, efficient resource management, and the ability to create isolated environments within the cloud.
"Remote IoT VPC network example" is not just a buzzword but a strategic imperative in today's tech-driven world. It offers a robust solution for businesses that seek secure and scalable cloud networking, ensuring data privacy and enabling efficient resource management.
Consider this scenario: You are a Raspberry Pi enthusiast eager to integrate your projects with the cloud. Combining Remote IoT and VPC networks with Raspberry Pi provides a secure and scalable foundation for your IoT projects. With a VPC, you can create subnetworks, configure IP ranges, and establish controlled communication between your devices.
A core benefit of adopting Remote IoT VPC Networks is the ability for organizations to effectively manage their devices while maintaining stringent security and compliance standards. This approach ensures that your IoT ecosystem remains secure and well-governed.
RemoteIoT enables you to securely connect and manage machines and devices from anywhere in the world. This ability is especially valuable in today's work environment. You can even connect to devices behind firewalls using encrypted SSH tunnels. This encrypted tunnel protects your data from prying eyes. No one can read the data in the tunnel, not even RemoteIoT.
The RemoteIoT API further enhances automation and integration of the RemoteIoT service into your system. These web services allow you to access your device from anywhere.
If you're diving into the world of remote IoT VPC network examples, you've come to the right place. This isn't just about setting up a connection; it's about creating a secure, scalable, and efficient network that can handle the demands of modern IoT devices.
For Raspberry Pi enthusiasts, leveraging a VPC ensures robust security and scalability for IoT projects. Remote IoT VPC networks enable organizations to manage their devices effectively while maintaining security and compliance.
To successfully set up a remote IoT VPC network, you must understand several core components:
1. Cloud Provider Selection:
Choose a reliable cloud provider like Amazon Web Services (AWS), Microsoft Azure, or Google Cloud Platform (GCP). AWS is frequently used due to its comprehensive IoT services and robust VPC capabilities.
2. VPC Configuration:
Within your chosen cloud provider, set up a Virtual Private Cloud (VPC). Define the IP address range for your VPC (e.g., 10.0.0.0/16).
3. Subnet Creation:
Create subnets within your VPC. Subnets divide your VPC into smaller, manageable networks. Consider creating both public and private subnets. Public subnets can host devices that need internet access, while private subnets are for devices that should not be directly accessible from the internet.
4. Internet Gateway:
If your IoT devices need to communicate with the internet, you'll need an Internet Gateway (IGW). This allows traffic to flow in and out of your VPC.
5. Routing Tables:
Configure routing tables to direct network traffic. Each subnet must be associated with a routing table that specifies where traffic should be sent. For example, traffic destined for the internet should be routed through the Internet Gateway.
6. Security Groups:
Use security groups to control inbound and outbound traffic to your IoT devices. Security groups act as virtual firewalls, allowing you to specify which types of traffic (e.g., SSH, HTTP, MQTT) are permitted.
7. Network ACLs (Optional):
Network Access Control Lists (ACLs) provide an additional layer of security. They act as firewalls at the subnet level, allowing you to control traffic flow more granularly.
8. IoT Device Configuration:
Configure your IoT devices to connect to the VPC. This typically involves assigning static IP addresses within the VPC's IP range or using DHCP. Ensure your devices are configured to use the correct gateway and DNS settings.
9. SSH Access (for Raspberry Pi):
For Raspberry Pi devices, you may want to enable SSH access for remote management. Ensure SSH is enabled on the Raspberry Pi and that security groups allow SSH traffic (port 22).
10. Remote Access Tools:
Use remote access tools like RemoteIoT to securely connect to your devices. RemoteIoT provides an encrypted SSH tunnel, ensuring that your data remains private and secure.
11. Monitoring and Management:
Implement monitoring tools to track the health and performance of your IoT devices and network. Use cloud provider-specific tools or third-party solutions to monitor network traffic, CPU usage, and other metrics.
12. Scalability and Automation:
Design your network with scalability in mind. Use automation tools (e.g., infrastructure as code) to easily deploy and manage additional devices and resources as your needs grow.
| Key Components | Description |
|---|---|
| VPC | A logically isolated section of the cloud provider's network. |
| Subnets | Subdivisions of the VPC, allowing for organization and control. |
| Internet Gateway | Enables communication with the public internet. |
| Routing Tables | Direct network traffic within the VPC and to the internet. |
| Security Groups | Act as virtual firewalls to control inbound and outbound traffic. |
| Network ACLs | Provide an additional layer of security at the subnet level. |
| IoT Devices | Devices connected to the VPC, such as Raspberry Pi. |
| Remote Access Tools | Tools like RemoteIoT for secure remote access. |
| Monitoring Tools | Track the health and performance of your devices and network. |
The concept of a remote IoT VPC network has become increasingly significant for businesses and developers in today's digital age.